Product Description
Boost your ISO 27001:2022 GRC with over 120 pre-built templates covering risks, policies, and documentation, simplifying your journey to achieve and maintain robust information security certification. Navigating the intricate landscape of information security management can be a daunting task. The ISO 27001:2022 standard, while essential for safeguarding your organization’s valuable assets, presents a complex web of requirements, policies, and procedures. But what if you could simplify this process, turning a potential hurdle into a strategic advantage? The answer lies in eStreet Security’s ISO 27001:2022 Compliance Documentation Toolkit.
(All-in-One) ISO 27001:2022 Compliance Toolkit by eStreet Security – Your Path to Effortless GRC and Policy Compliance
Conquer the complexities of information security management with the ISO 27001 Toolkit, developed by the very experts who pioneered ISO 27001 certification.
Built for Seamless Compliance: Leverage the power of proven ISO 27001-compliant documentation, honed through years of real-world experience. Stay ahead of the curve with over 500 annual updates through our DocumentKits platform, ensuring you always meet the latest standards and regulations. Our technical advisors continually track changes in best practices and requirements, keeping your toolkit up-to-date.
Simplify Implementation and Save: Access and edit your templates anytime, anywhere, on any device thanks to cloud-based convenience and our mobile apps on the Apple app store and Google play store. Effortlessly customize by adding your company logo and details with a click, auto-populating throughout your documents. Helpful tooltips and examples guide you through the customization process, ensuring clarity and accuracy. Collaborate seamlessly with up to 10 users, sharing the workload and ensuring consistency.
Customer-Focused and Results-Driven: We actively seek customer feedback to refine and enhance our toolkits, making compliance even easier. Reduce duplication and effort by seamlessly integrating with other toolkits in our range. Build a comprehensive management system effortlessly with our shared document feature.
Introducing eStreet Security’s ISO 27001:2022 Risk, Policy, and Compliance Toolkit – the definitive solution designed to streamline your compliance journey.
Your Fast Track to Certification & Continuous Improvement
Our award-winning toolkit isn’t just another set of templates. It’s a meticulously crafted roadmap, created by a seasoned global team of CISSP-certified auditors with over 30 years of hands-on experience. This expertise ensures that our toolkit isn’t just comprehensive, it’s practical, user-friendly, and tailored to the real-world challenges organizations face.
Who Can Benefit:
- Small and Medium-Sized Enterprises (SMEs): Our toolkit levels the playing field, making ISO 27001 compliance accessible and achievable for organizations of all sizes.
- Large Enterprises: Streamline your compliance efforts, reduce complexity, and ensure consistency across your organization.
- IT and Security Teams: Save valuable time and resources by leveraging our pre-built templates and expert guidance.
- GRC Professionals: Simplify your compliance management and reporting processes.
- Consultants: Offer your clients a comprehensive and efficient solution for ISO 27001 compliance.
Why Choose eStreet Security’s Toolkit?
- Unmatched Expertise: Benefit from decades of insider knowledge distilled into 120+ easy-to-use Microsoft Office templates, covering policies, procedures, controls, checklists, and more.
- Complete Coverage: From regulatory compliance to risk management, we’ve got you covered with every document you need for ISO 27001:2022 certification and ongoing ISMS improvement.
- Proven Success: Our toolkit has helped countless organizations streamline their compliance efforts, save valuable time and resources, and achieve lasting security results.
- Clear Adaptable Guidance: Detailed examples and highlighted text make it simple to tailor each document to your specific organizational needs. We understand that every organization is unique. That’s why our templates are fully customizable, allowing you to tailor them to your specific needs, industry, and regulatory requirements.
- Full Sample Documents: Get a head start on implementation with complete examples that demonstrate best practices.
- Complete Compliance: Ensure full alignment with the latest ISO 27001:2022 requirements, saving you valuable time and resources.
- 120+ Customizable Templates: Easily tailor the documents to fit your organization’s unique needs and context. Say goodbye to starting from scratch. Our toolkit includes over 120 meticulously designed templates covering every aspect of ISO 27001 compliance, from risk assessments and policies to incident response plans and supplier agreements.
More Reasons to eStreet Security’s Compliance Toolkit as part of your ISO certification efforts?
- Expert Guidance from eStreet Security: Benefit from our team’s deep expertise in information security, GRC, and compliance as you implement your ISMS. Our templates are infused with the knowledge and best practices gleaned from decades of experience in the field. You’ll benefit from clear instructions, helpful tips, and real-world examples to guide you through the implementation process
- Time & Cost Savings: Our toolkit empowers your team to take charge of your ISMS implementation, minimizing the need for expensive external consultants. By streamlining the process, you’ll achieve ISO 27001 compliance faster and more cost-effectively, maximizing your ROI.
- Risk Reduction & Enhanced Security: Strengthen your information security posture and protect your organization from cyber threats with eStreet Security’s proven methodologies. Our toolkit helps you identify and mitigate risks proactively, strengthening your security posture and protecting your critical assets.
- Increased Efficiency: Streamline your ISMS and GRC processes to improve operational efficiency, eliminate redundancies, and enhance collaboration across IT, HR, security, legal, and compliance departments.
- Demonstrable Due Diligence: Provide evidence of your commitment to information security and GRC to stakeholders and regulators.
- Audit trail: Record actions and measure improvements for certification and audits.
- Enhanced Reputation: Demonstrate your commitment to information security and gain a competitive edge in the market.
- Instant Access: Download the complete toolkit immediately after payment for quick and easy implementation and start your journey to compliance today.
- Record progress: Keep track of task progress and outstanding actions in the Implementation Manager document.
- Lifetime Access and Updates: Your purchase grants you lifetime access to the toolkit, ensuring you always have the latest versions and updates, even as the standard evolves.
What’s Inside:
120+ Professionally Designed Compliance Document Templates
All 120+ compliance document templates are aligned with ISO 27001:2022, NIST CSF, ISO 22301, PCI-DSS, and HIPAA as well as the following prominent standards in information security:
- ISO27001:2013
- ISO/IEC 27002
- ISO/IEC 27005
- ISO/IEC 27017
- ISO/IEC 27018
- ISO/IEC 27701
- ISO/IEC 27032
- ISO/IEC 27035
- ISO/IEC 20000
- ISO 9001:2015
- NIST SP 800-53
- NIST SP 800-171
- NIST Cybersecurity Framework (CSF)
- NIST SP 800-37
- NIST SP 800-30
- CIS Controls (Center for Internet Security Controls)
- PCI DSS 4.0 (Payment Card Industry Data Security Standard)
- COBIT (Control Objectives for Information and Related Technologies)
- HIPAA (Health Insurance Portability and Accountability Act)
- GDPR (General Data Protection Regulation)
- FISMA (Federal Information Security Management Act)
- SOX (Sarbanes-Oxley Act)
- SOC 2 (Service Organization Control 2)
- SOC 1 (Service Organization Control 1)
- ITIL (Information Technology Infrastructure Library)
- CMMC (Cybersecurity Maturity Model Certification)
- OWASP (Open Web Application Security Project) Top Ten
- CSA CCM (Cloud Security Alliance Cloud Controls Matrix)
- BSI IT-Grundschutz (German Federal Office for Information Security)
- ISF (Information Security Forum) Standard of Good Practice
- IEC 62443 (Industrial Network and System Security)
- FIPS 140-2 (Federal Information Processing Standard)
- SWIFT CSP (SWIFT Customer Security Programme)
- NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection)
- ENISA (European Union Agency for Cybersecurity) Recommendations
- AS/NZS ISO/IEC 27001 (Australian/New Zealand Standard for Information Security Management)
- ANSI/ISA 99 (Industrial Automation and Control Systems Security)
- IAPP (International Association of Privacy Professionals) Privacy Framework
- ITSG-33 (Canadian Centre for Cyber Security IT Security Guidance)
- CERT-RMM (Resilience Management Model)
- HITRUST CSF (Health Information Trust Alliance Common Security Framework)
- APRA CPS 234 (Australian Prudential Regulation Authority Cyber Security Standard)
- MAS TRM (Monetary Authority of Singapore Technology Risk Management)
- Basel III (International Banking Regulations)
- Cyber Essentials (UK Government Cyber Security Certification)
- FFIEC IT Examination Handbook (Federal Financial Institutions Examination Council)
- NIST SP 800-88 (Guidelines for Media Sanitization)
- ISO 31000 (Risk Management)
- IEC 61508 (Functional Safety of Electrical/Electronic/Programmable Electronic Safety-related Systems)
- TISAX (Trusted Information Security Assessment Exchange).
These standards collectively encompass various aspects of organizational information security, including risk management, data protection, cybersecurity, and compliance with regulations.
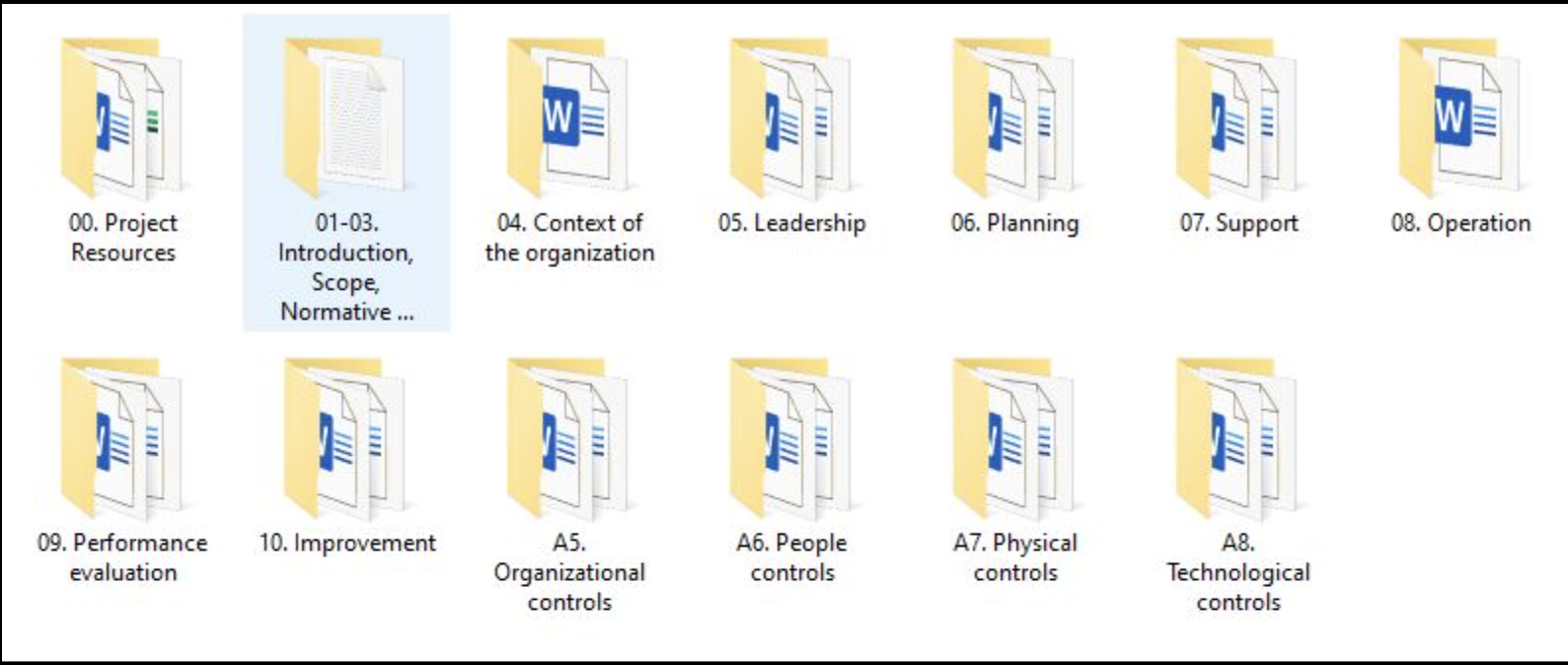
Intuitive Folder Structure for Effortless Navigation
Our toolkit is designed with your convenience in mind. The clear folder structure mirrors the ISO 27001:2022 standard’s clauses, making it easy to locate and reference the documents you need:
- 0.0 Project Resources: Kickstart your implementation with essential project planning and management documents.
- 01-03: Establish the foundation of your ISMS with documents covering Introduction, Scope, Normative References, and Terms and Definitions.
- 04: Define the context of your organization and its information security needs.
- 05: Outline leadership roles and responsibilities for effective ISMS governance.
- 06: Develop a comprehensive plan for implementing and maintaining your ISMS.
- 07: Ensure adequate support for your ISMS, including resources, competence, awareness, and communication.
- 08: Document the operational aspects of your ISMS, including risk assessment and treatment.
- 09: Monitor, measure, analyze, and evaluate your ISMS performance.
- 10: Continually improve your ISMS based on performance evaluation results.
- A5: Establish and maintain organizational controls for effective information security management.
- A6: Manage the security of your human resources.
- A7: Implement physical security controls to protect your assets.
- A8: Deploy technological controls to safeguard your information systems and networks.
This logical structure ensures you can quickly find the right documents at the right time, saving you valuable time and effort throughout your ISO 27001:2022 journey.
List of all ISO 27001:2022 documents:
Don’t waste time reinventing the wheel. Let eStreet Security’s ISO 27001:2022 Risk, Policy & Compliance Toolkit be your trusted guide to a secure and compliant future. This toolkit provides comprehensive documentation covering organizational controls, people controls, physical controls, and technological controls, as well as regulatory, governance, audit, and certification documents to support your compliance journey.
- Information Security Management System PID.docx
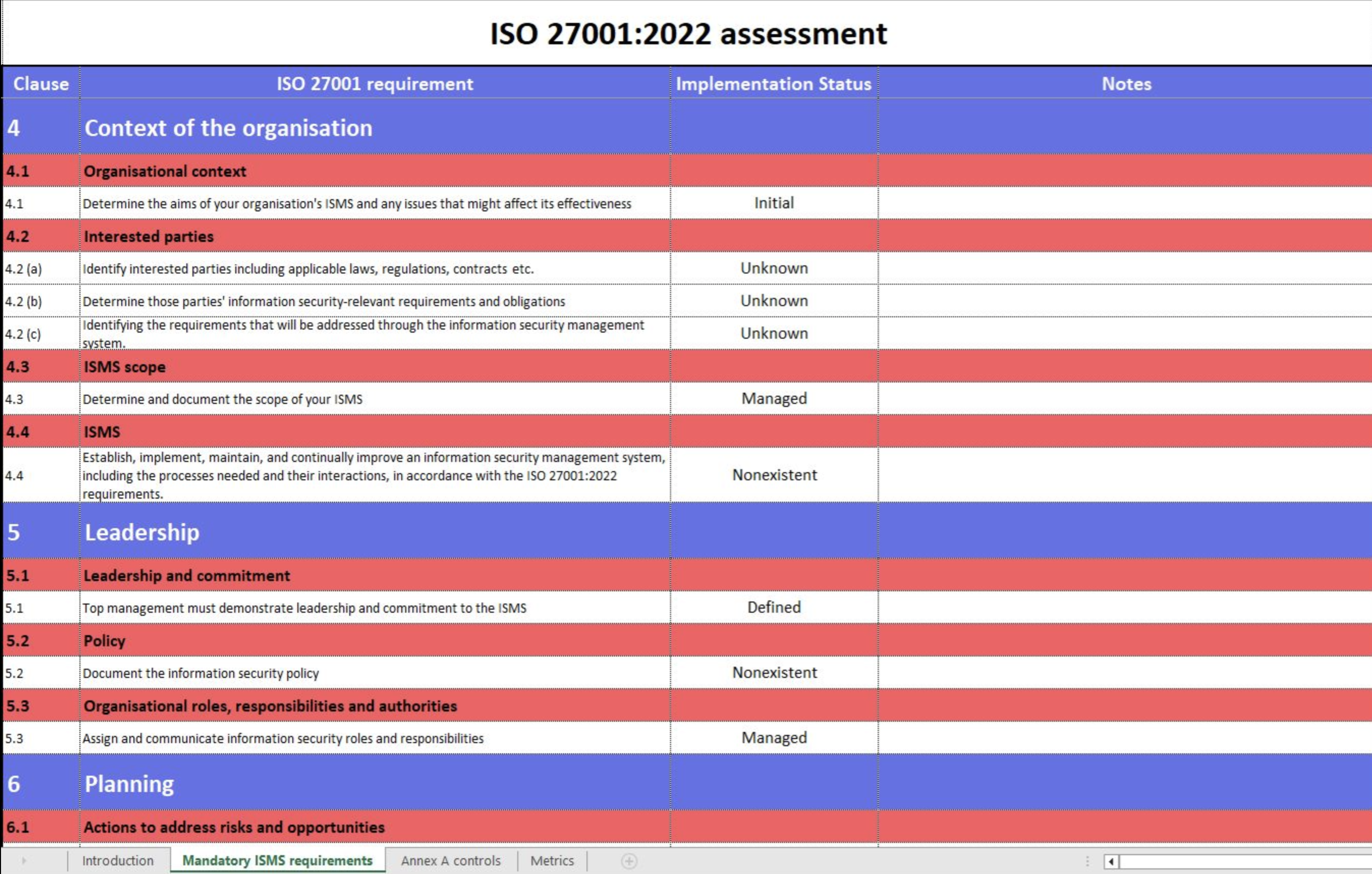
- ISO 27001-2022 Assessment Tool.xlsx
- ISO-IEC 27001 Benefits Presentation.pptx
- ISO-IEC 27001 Project Plan.xlsx
- ISO27001 Highlight Report.docx
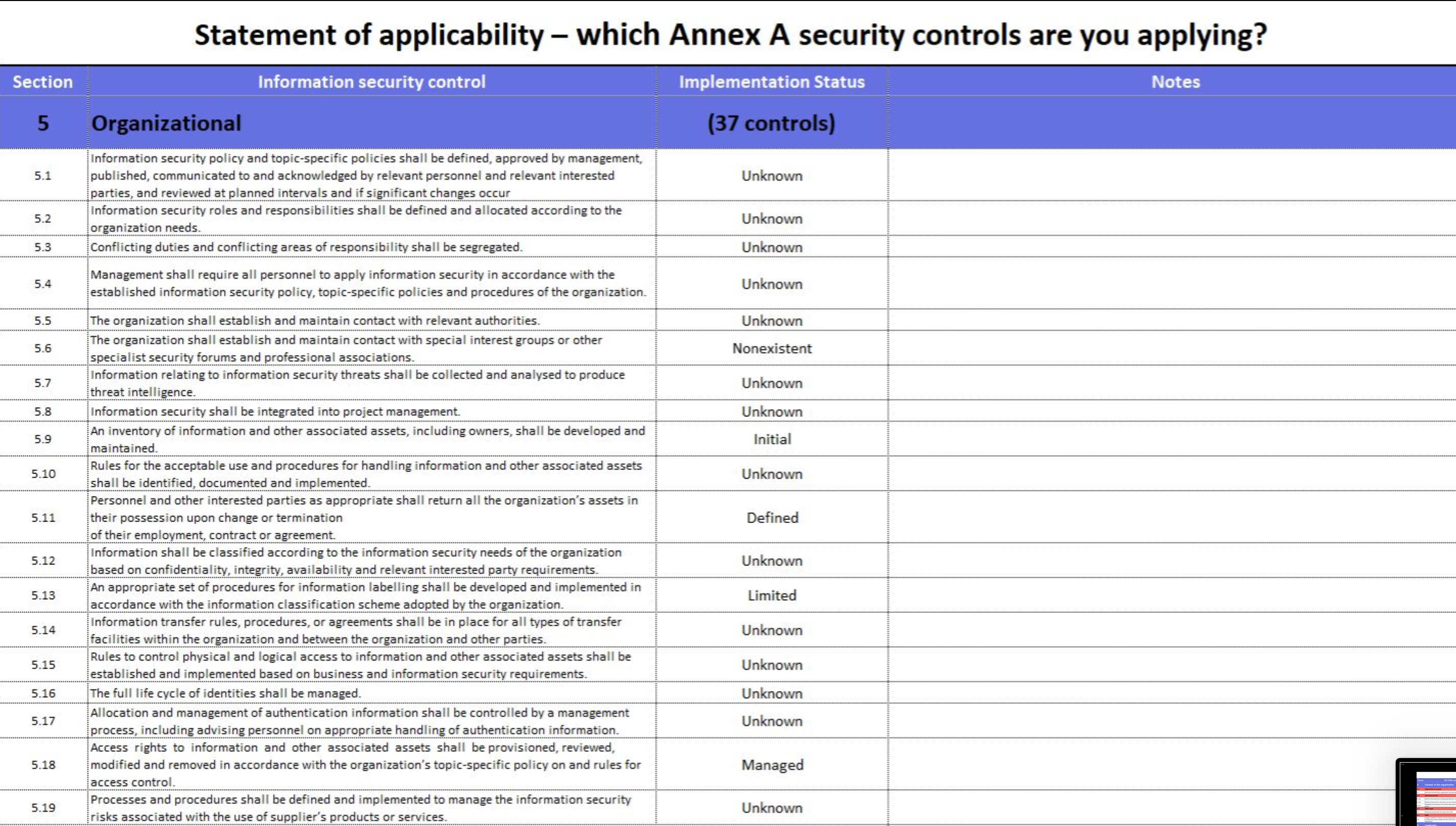
- ISO27001-2022 Statement of Applicability.xlsx
- ISO 27001 Audit Checklist.xlsx
- Information Security Context, Requirements and Scope.docx
- Executive Support Letter.docx
- Information Security Management System Policy.docx
- Information Security Roles Responsibilities and Authorities.docx
- Top Management Communication Programme.docx
- Meeting Minutes Template.docx
- Information Security Management Plan.docx
- Risk Assessment and Treatment Process.docx
- Information Security Risk Assessment Report.docx
- Information Security Risk Treatment Plan.docx
- Procedure for the Control of Documented Information.docx
- Procedure for the Control of Records.docx
- Information Security Communication Plan.docx
- Information Security Skills and Training Needs Assessment.docx
- Supplier Information Security Evaluation Process.docx
- Procedure for Information Security Management System Audits.docx
- Internal Audit Action Plan.docx
- Information Security Review Meeting Agenda.docx
- Process for Monitoring, Measurement, Analysis and Evaluation.docx
- Information Security Management System Audit Plan.docx
- ISMS Audit Programme Schedule.docx
- ISO 27001 Internal Audit Checklist
- Procedure for Continual Improvement.docx
- Procedure for the Management of Nonconformity.docx
- ISMS Continual Improvement Action Log.xlsx
- Information Security Policy.docx
- Information Security Guidelines for Project Management.docx
- Segregation of Duties Guidelines.docx
- Information Security Classification Guidelines.docx
- Information Security Labelling Procedure.docx
- Procedure for the Disposal of Media.docx
- Asset Handling Procedure.docx
- Access Control Policy.docx
- User Access Management Process.docx
- Procedure for Remote Supplier Access to Systems.docx
- Procedure for the Reset of User Passwords.docx
- Operating Procedure.docx
- Information Transfer Agreement.docx
- Information Transfer Procedure.docx
- Network Services Agreement.docx
- Supplier Management Policy.docx
- Supplier Information Security Agreement.docx
- Information Security Incident Management Procedure.docx
- Incident Management Process.docx
- Major Incident Management Process.docx
- Business Continuity Exercising and Testing Schedule.docx
- Business Continuity Plan.docx
- Business Continuity Test Plan.docx
- Business Continuity Test Report.docx
- Business Impact Analysis Process.docx
- Incident Response Procedure.docx
- Post Incident Report Template.docx
- Legal Responsibilities Policy.docx
- Legal and Regulatory Requirements Procedure.docx
- IP and Copyright Compliance Policy.docx
- Records Retention and Protection Policy.docx
- Threat Intelligence Policy.docx
- Information Security Policy for the use of Cloud Service.docx
- Remote Working Policy.docx
- AUP and Personal Commitment Statement.docx
- Email Policy.docx
- Internet Acceptable Use Policy.docx
- Employee Termination and Change of Employment Checklist.docx
- Employee Recruitment and New Starter Checklist.docx
- Employee Screening Checklist.docx
- Guidelines for Inclusion in Employment Contracts.docx
- Employee Disciplinary Process.docx
- Non-Disclosure Agreement.docx
- Leavers Letter.docx
- Procedure for the Management of Removable Media.docx
- Removable Media Assessment Guidelines.docx
- Physical Media Transfer Procedure.docx
- Configuration Management Process.docx
- Configuration Management Procedure.docx
- Guidelines for Working in Secure Areas.docx
- Physical Security Design Standards.docx
- Procedure for Taking Assets Offsite.docx
- Physical Security Policy.docx
- Change Request Form.docx
- Mobile Computing Policy.docx
- Bring Your Own Device Policy.docx
- Cryptographic Policy.docx
- Backup Policy.docx
- Procedure for Monitoring the Use of IT Systems.docx
- Capacity Management Process.docx
- Change Management Policy.docx
- Change Management Process.docx
- Service Level Agreement.docx
- Capacity Plan.docx
- Software Policy.docx
- Anti-Malware Policy.docx
- Release and Deployment Management Policy.docx
- Release and Deployment Management Process.docx
- Release and Deployment Plan.docx
- Technical Vulnerability Management Policy.docx
- Information Systems Audit Plan.docx
- Technical Vulnerability Assessment Procedure.docx
- Network Security Policy.docx
- Design and Transition of New or Changed Services Process.docx
- Business Requirements Specification.docx
- Project Initiation Document.docx
- Project Highlight Report.docx
- Project Post Implementation Review.docx
- Service Acceptance Checklist.docx
- Secure Development Policy.docx
- Secure Development Environment Guidelines.docx
- Principles for Engineering Secure Systems.docx
- Availability Management Plan.docx
- Secure Informtion Deletion Policy.docx
- Data Masking Policy.docx
- Data Leakage Prevention Policy.docx
- Event Logging and Monitoring Policy.docx
- Safe Browsing and Web Filtering Policy.docx
- Secure Coding Policy.docx
Safeguard your organization’s valuable information assets and achieve ISO 27001:2022 certification with confidence using eStreet Security’s meticulously crafted documentation toolkit. Our comprehensive package equips you with 120+ expertly designed templates, policies, procedures, and forms, meticulously addressing every facet of your Governance, Risk, and Compliance (GRC) efforts and Information Security Management System (ISMS) policies.

Who Should Use This Toolkit:
The eStreet Security compliance toolkit for ISO 27001:2022 is for cyber security professionals or any personnel responsible for implementing or maintaining an ISO 27001:2022 compliant ISMS, as well as GRC professionals, documenting these frameworks, standards, and regulations typically involves the following cybersecurity roles:
Core Roles:
- Information Security Manager/Officer (CISO/ISO): Overall responsibility for the information security program and ensuring compliance.
- Information Security Analyst: Conducts risk assessments, develops policies and procedures, and implements controls.
- Information Security Auditor: Assesses the effectiveness of controls and compliance with standards.
- Security Architect: Designs and implements security solutions to meet requirements.
- Security Engineer: Implements and maintains security tools and technologies.
- Security Consultant: Provides expert advice on security matters and assists with compliance efforts.
Specialized Roles (depending on the standard/framework):
- Privacy Officer: Ensures compliance with data privacy-focused regulations like GDPR and HIPAA.
- Compliance Analyst/Officer: Specializes in compliance with specific regulations or industry standards.
- Data Protection Officer: Oversees data protection and privacy compliance.
- Risk Manager: Identifies, assesses, and mitigates information security risks.
- Incident Responder: Responds to and investigates security incidents.
- Digital Forensics Analyst: Collects and analyzes digital evidence in the event of a security breach.
- Cybersecurity Lawyer: Provides legal advice on cybersecurity matters.
- Technical Writer: Creates and maintains security documentation.
Supporting Roles:
- IT Manager/Network Administrator: Supports the implementation and maintenance of security controls.
- System Administrator: Manages and maintains systems to ensure their security.
- Database Administrator: Secures and manages databases.
- Software Developer: Develops secure software applications.
Note: The specific roles involved in documenting compliance can vary depending on the organization’s size, structure, and the complexity of the standards or frameworks being addressed. Smaller organizations may combine some roles, while larger organizations may have dedicated teams for each.
How to Use This ISO 27001:2022 Compliance Document Toolkit: A Step-by-Step Guide
-
Purchase and Download: Right after payment, you can instantly download the toolkit from:
- The eStreet Security web app at: https://app.estreetsecurity.com/
- The eStreet Security mobile app on the Apple App Store or Google Play Store

Get certified faster with eStreet Security’s ISO 27001 toolkit. Achieve ISO 27001:2022 effortlessly. Our GRC toolkit offers 120+ templates: risk, policy, and essential documentation. Start now!
-
Identify Your Needs: Determine which standards and regulations your organization must comply with (e.g., ISO 27001, GDPR, NIST CSF).
-
Browse the Templates: Explore the toolkit to find the templates that align with your identified requirements.
-
Customize: Adapt the templates to fit your organization’s specific context, policies, and procedures. Replace placeholders with relevant information and tailor the language to match your style guide.
-
Implement: Integrate the completed documents into your existing information security management system (ISMS) or governance, risk, and compliance (GRC) program.
-
Review and Update: Regularly review and update your compliance documentation to ensure it remains current and accurately reflects your organization’s practices.
-
Train Your Team: Ensure that relevant staff members are familiar with the updated documentation and understand their roles in maintaining compliance.
Lifetime Access and Updates:
Rest assured that you’ll always have the latest versions of the toolkit, even when ISO standards get updated. Simply log in to your eStreet Security account and re-download the updated toolkit at no extra charge. Your purchase grants you lifetime access and peace of mind knowing you’re always compliant.
Additional Tips:
- Seek Expert Advice: If you have questions or need assistance with customization, consult with a cybersecurity professional or legal expert.
- Collaborate: Involve relevant stakeholders, such as IT, legal, and compliance teams, in the documentation process.
- Use a Version Control System: Keep track of changes and revisions to your documents using a version control system.
By following these steps and leveraging the lifetime access and updates, you can confidently maintain a robust and up-to-date compliance posture for your organization.
With years of experience in the information security field, eStreet Security has a proven track record of helping organizations achieve and maintain compliance with international standards. Our team of experts understands the challenges you face and is dedicated to providing you with the support and resources you need to succeed.
Identify Your Path to Compliance with eStreet Security’s Gap Assessment Checklist:
Unsure where to begin? Our toolkit includes a detailed Gap Assessment Checklist to help you pinpoint areas for improvement and prioritize your compliance efforts. By evaluating your current information security practices against the ISO 27001:2022 requirements, you can develop a clear roadmap for achieving certification and strengthening your overall security posture.
Take the first step towards a robust and effective ISMS and comprehensive GRC program. Invest in eStreet Security’s ISO 27001:2022 Risk, Policy and Compliance Documentation Toolkit today and experience the benefits of a streamlined and secure information security management system.


Reviews
There are no reviews yet.